Why SMBs Need a Clear Map in an Evolving Cyber Landscape
For small and mid-sized businesses (SMBs), cybersecurity has become as much a leadership challenge as a technical one. In recent years, the cyber threat landscape has evolved faster than most organizations’ ability to adapt. A single attack can halt operations, drain financial resources, and permanently erode customer trust.
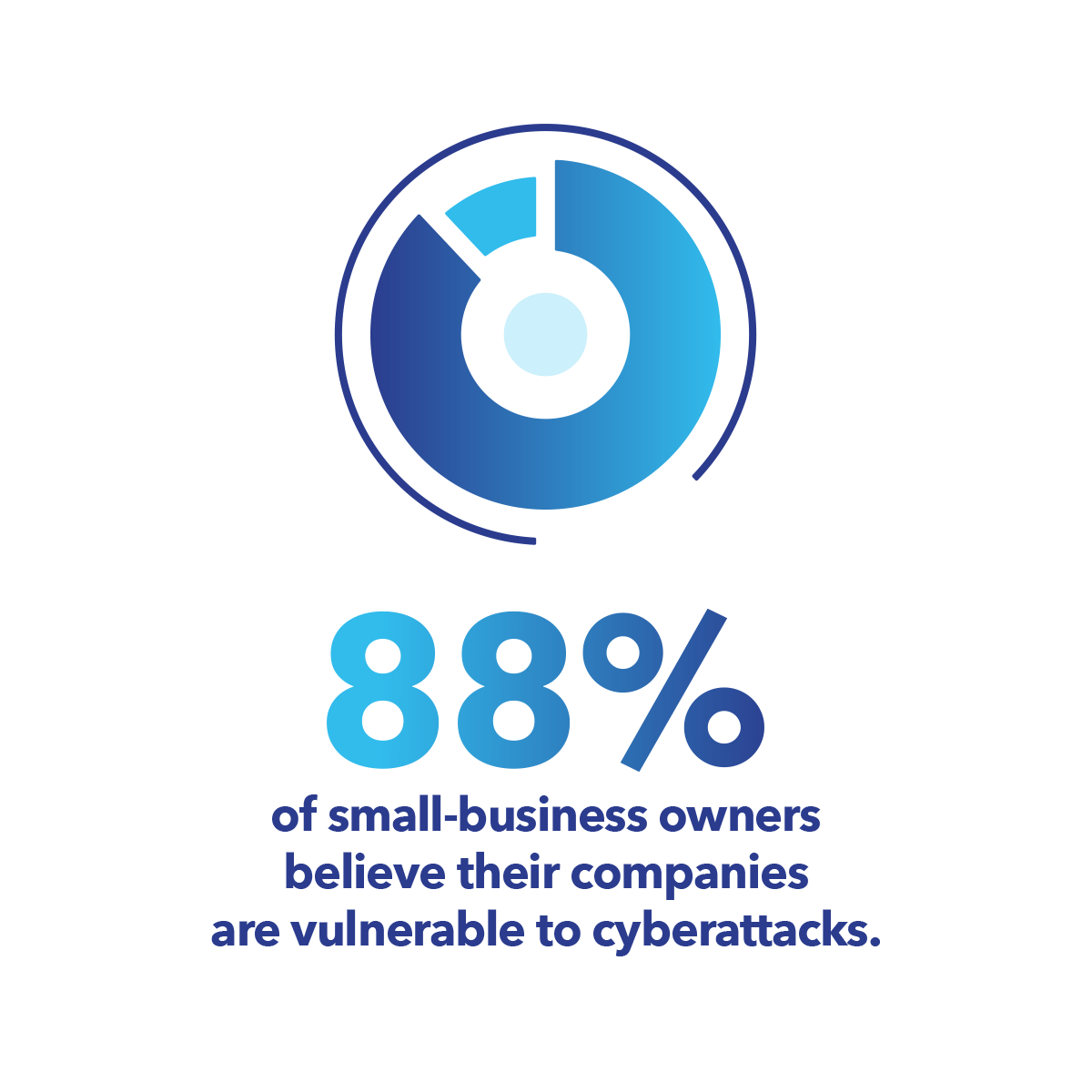
According to the U.S. Small Business Administration (SBA), 88% of small-business owners believe their companies are vulnerable to cyberattacks, yet more than half lack a formal incident response plan. In 2025 alone, ransomware incidents surged by more than 40% among regional service providers and healthcare networks, targeting organizations that often lacked the structure or visibility to detect and contain threats early.
For most SMBs, the problem isn’t awareness, it’s bandwidth and structure. Leaders understand the risk but struggle to translate cybersecurity frameworks into daily operations. Security tools are in place but often in isolation, leaving gaps in detection, response, and recovery. What’s missing is a strategic blueprint that connects technology, processes, and people.
This is where the Cyber Defense Matrix, developed by cybersecurity strategist Sounil Yu, comes in. It organizes the chaos of cybersecurity into a structured visual model that maps every control and process across the five NIST Cybersecurity Framework (CSF) functions (Identify, Protect, Detect, Respond, and Recover) and the key asset categories: Users, Devices, Applications, Networks, and Data. The result is clarity: the ability to see your organization’s defensive posture and pinpoint where improvement is needed most.
For SMB leaders, the Cyber Defense Matrix offers a roadmap for action, a way to measure maturity, prioritize investments, and know when to engage an MSP (Managed Service Provider) for deeper support and scalability.
In this context, organizations like Ardham Technologies stand out as trusted partners helping businesses turn frameworks into execution. By integrating the Cyber Defense Matrix into its holistic approach, Ardham bridges infrastructure, security, and strategy helping clients move from awareness to resilience and turn cybersecurity from a cost center into a growth enabler.
1. Understanding the Matrix: From Framework to Function
The Cyber Defense Matrix bridges the gap between theory and execution. It provides a visual structure that connects the abstract language of frameworks like NIST CSF and ISO/IEC 27001 to practical operational decisions.
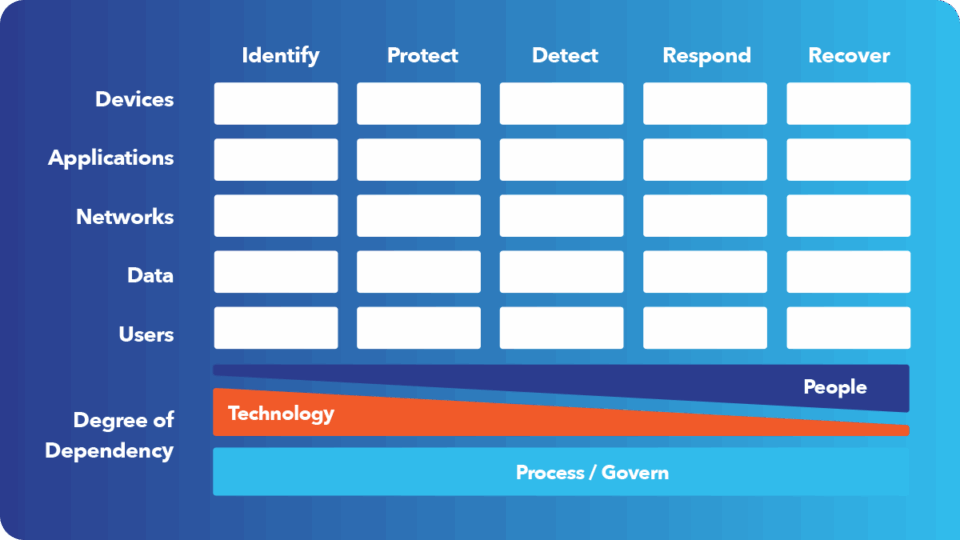
The Matrix consists of a grid created by two axes. The horizontal axis aligns with the five foundational NIST functions that represent different aspects of cybersecurity preparedness:
- Identify: Know what assets exist (hardware, software, data, and roles) and understand their value and exposure.
- Protect: Apply safeguards like encryption, firewalls, and multi-factor authentication (MFA) to prevent compromise.
- Detect: Use monitoring tools and analytics to spot anomalies in real time.
- Respond: Establish a tested plan for isolating incidents, notifying stakeholders, and mitigating damage.
- Recover: Restore operations swiftly through secure, validated backups and defined recovery objectives.
The vertical axis is comprised of key areas of any organization to address cybersecurity readiness:
- Devices: Encompasses all physical and virtual assets (servers, laptops, and IoT devices). Protection begins with full visibility, consistent patching, and endpoint encryption.
- Applications: Includes both on-premises and cloud software. Secure coding, access controls, and timely patching keep vulnerabilities from spreading.
- Networks: The backbone connecting users and data. Segmentation, firewalls, and a zero-trust model ensure every connection is verified.
- Data: The ultimate target of most attacks. Classification, encryption, and data loss prevention tools safeguard sensitive information.
- Users: The first and last line of defense. MFA and security-awareness training turn people into active participants in protection.
Completing the Matrix
Once the rows (asset categories) and columns (cybersecurity functions) are defined, the real value of the Cyber Defense Matrix emerges in how it helps organizations visualize coverage and gaps.
To complete the Matrix, leaders should start by mapping all existing tools, processes, and policies into their corresponding cells. For instance, MFA enforcement might fall under Protect/Users, while backup validation belongs in Recover/Data. Each intersection between a function and an asset type represents a control area revealing not only what’s covered but also what’s missing.
Organizations often discover “blind spots”: areas where they’ve invested heavily in protection but little in detection or recovery. This exercise transforms cybersecurity from a collection of disjointed technologies into an integrated strategy.
A fully populated Matrix becomes a strategic dashboard. It helps executives prioritize investments based on risk, justify budgets with evidence, and align security initiatives with business objectives. When reviewed regularly, especially after incidents or infrastructure changes, the Matrix evolves from a static framework into a living tool for continuous improvement.
For SMBs, mapping existing tools and processes onto the Matrix often reveals both redundancies and gaps. You might discover overlapping endpoint protections but no formal recovery process, or strong network defenses but no data classification. That insight allows leaders to prioritize intelligently (based on impact, not panic), a principle central to Ardham’s NIST-aligned approach.
Governance
The sixth dimension, Govern, underpins the entire model. As McKinsey explains in Competitive Advantage Through Cybersecurity: A Board-Level Perspective, cybersecurity must evolve beyond cost avoidance. When governance is embedded at board and executive levels, it becomes a strategic lever for trust, alignment, and performance. Governance ensures that every function in the Matrix operates with accountability, measurement, and alignment to organizational priorities.
2. Building from the Ground Up: Why IT Foundations Are Security Foundations
No defense can succeed without a stable IT foundation. Outdated infrastructure, unsupported software, and unpatched devices create vulnerabilities that even the most advanced detection tools cannot offset.
The Cybersecurity and Infrastructure Security Agency (CISA) reinforces this principle: resilience begins with modernization. Reliable, standardized systems reduce attack surfaces and streamline response. In other words, patching isn’t maintenance, it’s defense.
For SMBs with limited resources, modernization doesn’t need to happen all at once. Incremental improvements (such as migrating to secure cloud email, enforcing MFA, or segmenting networks) deliver measurable gains in both risk reduction and operational continuity.
They also improve eligibility for Cyber Liability Insurance, which increasingly rewards organizations with strong controls like MFA and incident response planning. In short, smart security investments pay off twice: reducing cyber risk and lowering insurance costs.
A real-world example: A mid-sized healthcare provider in Albuquerque adopted a Cyber Defense Matrix review after repeated phishing incidents. The audit revealed solid “Protect” measures (training, MFA) but gaps in “Identify” and “Recover.” With Ardham’s help, the organization implemented automated asset discovery and immutable backup systems creating measurable improvements in both visibility and recovery speed.
3. Operationalizing the Matrix: Turning Theory into Daily Practice
Understanding the Matrix is only the first step; operationalizing it is what builds resilience. The goal is to embed each NIST function into business operations, not as one-off tasks but as continuous disciplines.
For example, under Identify, SMBs can leverage lightweight asset discovery tools like Lansweeper or Microsoft Defender for Endpoint to maintain real-time visibility across their environment. Under Protect, extending MFA and least-privilege access to every user reduces attack vectors dramatically.
The Detect layer benefits from Extended Detection and Response (XDR) solutions such as SentinelOne, Microsoft Defender for Business, and Sophos, which consolidate telemetry from endpoints, networks, and cloud systems into a single view. For SMBs, that integration means faster, more coordinated incident response.
The Respond and Recover functions remain a major challenge for many smaller organizations. Less than two-thirds of mid-sized companies even have a formal incident response plan in place. Yet a simple playbook with clear escalation paths, communication templates, and post-incident reviews can dramatically reduce downtime. Aligning recovery objectives (RTO/RPO) with your core business priorities ensures continuity when (not if) a breach strikes.
At Ardham, this alignment becomes operational reality through integrated services that connect cybersecurity, backup, and infrastructure management; so the Cyber Defense Matrix isn’t just a framework but a living cybersecurity management system.
4. A Practical Checklist: Turning Structure into Strength
To make the Matrix actionable, SMB executives should reflect on five core questions:
- Visibility: Do we know which assets, users, and applications we’re protecting?
- Coverage: Which areas of the Matrix are unaddressed or rely on a single point of failure?
- Response Readiness: Have we tested our incident response plan in the last 12 months?
- Continuity: Are our backups isolated, encrypted, and recoverable within target RTOs and RPOs?
- Governance: Who owns cybersecurity decisions, and are they aligned with business risk tolerance?
Answering these questions transforms the Matrix from a static diagram into a continuous improvement process. It allows leaders to benchmark progress, communicate security posture in business terms, and demonstrate measurable value to stakeholders.
Organizations that follow this discipline often realize additional benefits: faster compliance audits, greater customer trust, and improved scores in cyber insurance assessments.
5. Lessons from New Mexico: Local Insights with Broader Impact
The Blue Cross and Blue Shield of New Mexico (BCBSNM) incident earlier this year illustrates a crucial truth for every leader: cybersecurity maturity is not a matter of size, budget, or reputation, it’s about how effectively governance translates policy into execution.
In this case, member data was exposed through a portal vulnerability, highlighting how even well-resourced organizations can face risk when visibility and accountability are fragmented. The breach demonstrated that strong technology alone isn’t enough; security must be anchored in clear ownership, structured response, and cross-functional coordination.
For SMBs, the lesson is clear. The Govern layer of the Cyber Defense Matrix (often overlooked) is what binds all other functions together. It connects technical controls with human responsibility, ensuring that detection and response don’t happen in silos.
Ardham Technologies helps organizations operationalize this layer by mapping governance structures against the Matrix and the NIST Cybersecurity Framework. Through this approach, they help identify high-impact actions such as vulnerability management, privileged access control, and recovery validation, all within realistic budgets.
By applying these principles, SMBs across New Mexico can strengthen resilience, protect customer trust, and turn cybersecurity governance into a measurable business advantage.
From Awareness to Action
In today’s landscape, frameworks like the Cyber Defense Matrix are no longer optional—they’re the operating system of resilience. They bring clarity to complexity, structure to chaos, and accountability to decision-making.
But frameworks only work when operationalized. The SMBs that thrive are those that treat cybersecurity not as a compliance exercise, but as an investment in continuity, trust, and growth.
SMBs that adopt a consistent set of security practices are more likely to report success in “operating efficiently” that is, improving productivity and reducing unplanned work. Structure, in other words, pays dividends.
For SMB leaders ready to move from awareness to execution, the Cyber Defense Matrix offers the roadmap and partners like Ardham Technologies provide the expertise to make it real.
If your organization is ready to modernize its cybersecurity posture, align strategy with action, and build measurable resilience, contact Ardham’s cybersecurity team today.